From a prompt in chapter 10 (“Correspondence”) in Baehr and Cook’s book The Agile Communicator: Principles and Practices in Technical Communication (2015), I decided to take a closer look at all the emails I sent one day.
After work, I counted the number of emails and then did some cursory data and content analysis to see if anything interesting emerged.
Totals
31 emails
2,315 words
4 screenshots
Next, I coded the contents to count based on categories of emails. I came up with four categories. The table below displays the categories and their counts:
Informational Reply 13
Research/Instructional Reply 8
Technical Question 6
Information Management Reply 4
Category descriptions
The following are brief descriptions for how I established the categories and how I think they demonstrate the typical professional correspondence of a technical writer (i.e., a technical writer in my industry, with my job responsibilities, etc.).
- Technical Question: This includes both SME and “Technical Review” meanings—that is, verifying that some information is accurate as well as allowed to publish. This would probably be different based on the technical writer’s status in the company and authority to publish with existing workflows.
- Informational Reply: General email reply such as answering a question “did you update XYZ?”
- Research/Instructional Reply: This is similar Informational Reply but there is a rhetorical difference – rhetorical in that it is framed as trying to gather more information (research), but is also points out information that the original poster missed.
- Information Management Reply: People don’t know what we can or can’t do and these emails clarify our capabilities to educate internal stakeholders what value we bring (e.g., Knowledgebase, Info Management) to the organization.
Analysis of the categories
I’m not surprised by the number and kind of emails that I sent during one workday. My most frequent emails were answering questions or providing information regarding my technical writing purview within my department. As an advocate for my department (and for techcomm in general), I also tend to reply to emails where I think there is an opportunity to not only clarify an issue, but also to provide information back to the original sender. The third most emails involved typical SME questions where I needed additional information to author a topic, or verification of a technical aspect of the product. The last category, “Information Management Reply” were mostly clarifications to people about misconceptions about what we can and can’t do – for the latter, that usually involved clarifying that a particular request was indeed a task or responsibility that my department owned, unbeknownst to the rest of the organization.
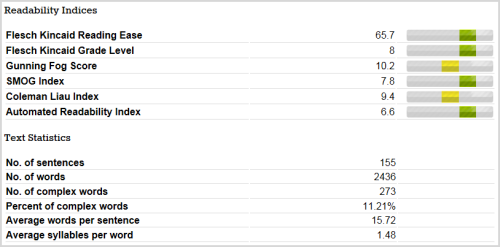
Readability of my emails
I performed a cursory readability analysis using an automated tool. The combined content of my emails had an average grade level of about 8 (US), meaning that it should be easily understood by 13 to 14 year olds.
Citation for the text
Baehr, C., and K. C. Cook. 2015. The Agile Communicator: Principles and Practices in Technical Communication. Kendall Hunt Publishing Company. https://books.google.com/books?id=XiLQsgEACAAJ.
If many technical writers could pool our emails together, do you think we would see similar categories emerge? Or are there too many professional variables involved? Would be an interesting project!